The rise of cybercrime has made a considerable impact on the global economy ($6 trillion in 2021), so much so that governments have deemed it relevant enough to include it in state national security agendas or that a U.S.-European program has been created.
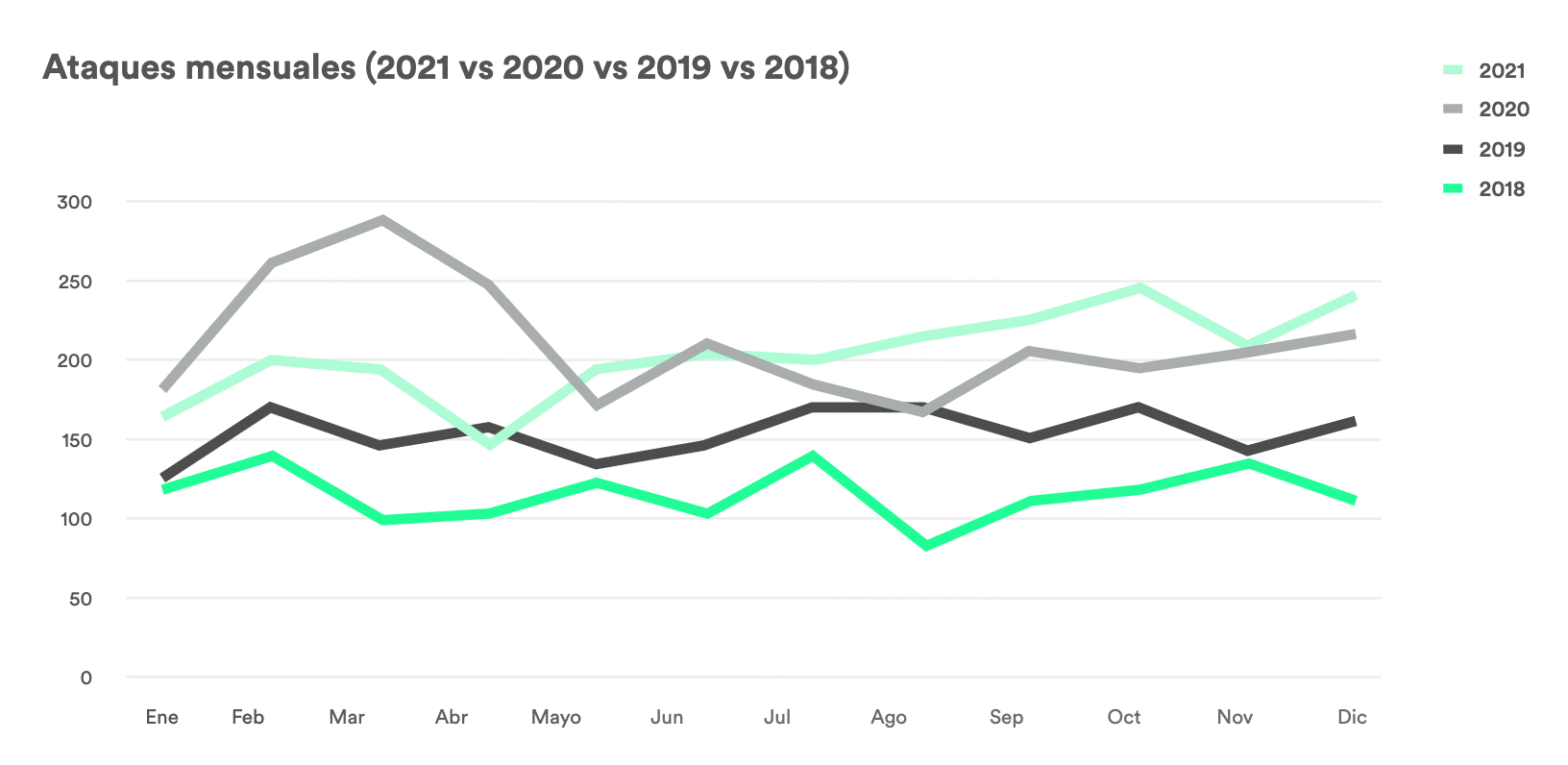
This is not surprising given the economic impact it generates, since the latest studies estimate that cybercrime moves more money than drug trafficking and many of the cybercriminal groups have an organized structure similar to that of drug trafficking. The level of professionalism has reached such an extent that cybercriminals offer themselves on certain dark web marketplaces and the term "eCrime as a Service" has been coined.
It is well known to all IT and information security managers that the arrival of the pandemic has only exacerbated an already existing problem, albeit in some cases latent in many organizations: the lack of information security in multiple variants.
The problems we encounter in companies can be grouped into several categories: