Over 94% of cyberattacks originate in the email inbox, with phishing (identity theft) being the main prong of attack. Phishing by means of a "whaling attack”, also known as "CEO fraud" has forced many companies not only to redefine authentication and certification processes, but also to try to prevent the effectiveness of these social engineering attacks at the point of origin: our email inbox.
First step: mail authentication protocols
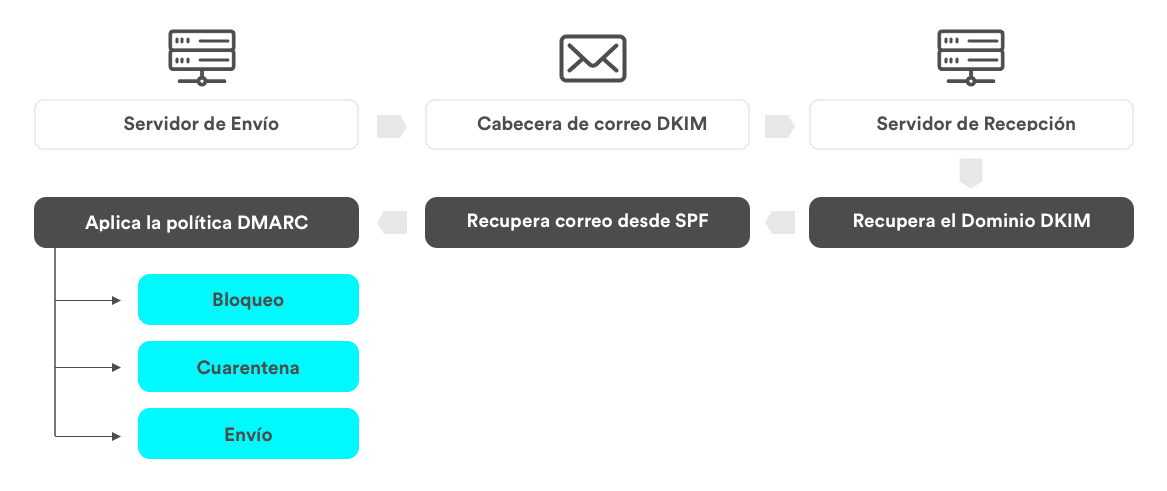
To effectively minimize the risk, it is advisable to implement a correct configuration of the so-called authentication protocols (SPF, DKIM and DMARC). These protocols verify the legitimacy of the sending servers and to improve the verification of the receipt of e-mails. They therefore serve both to protect us and to improve the protection of others.
To implement them, an audit of their status is carried out.
Email flow with protocols
Additional measures to mitigate risk
Sofistic, Cuatroochenta's cybersecurity area, has a team of professionals with extensive experience in consulting and specialized cybersecurity services, and can help you protect your email.
As a Microsoft Certified Cybersecurity Partner, Sofistic audits and secures the Microsoft 365 tenant for misconfigurations. To do this, they are not only based on the best practices recommended by Microsoft, but also on the extensive experience gained in multiple projects of this type. In addition, this assurance will serve as the basis for much more ambitious projects such as identity management, device management (MDM), and information tagging or leakage (DLP).