I must admit that when, on March 23, 2018 the e-Call (or ‘emergency call button’) was made mandatory in cars, I breathed a sigh of relief. In the event of an accident, the car automatically calls 112 (this can be activated manually) and sends data relating to the location, number of occupants of the vehicle, etc. By then, some cars already knew more about us than we did. That the vehicle is connected via telephone does not entail an extra cybersecurity risk, as one might initially think – come on, there is more risk when we leave it in the workshop and the mechanic connects to the switchboard with a computer that may have an outdated operating system, easily vulnerable to a third party, although we don’t consider this.

Imagination leads us to anticipate things that could possibly happen in the future… Have we done the same imaginative exercise regarding all the information that we have in our company, and without protection? After all, all companies have been connected for a long time – what is the result of someone accessing our computer system and having the formulation of our products, designs, the personal data of employees, customers, suppliers, at their disposal? Our financial information, or the configuration of all the robots on the production floor? And, above all, do we know the probability of that happening?
Source images www.smartpanel.com
Artificial intelligence (AI) – in a broad sense, and without distinction between machine learning, deep learning or neural networks and, in some cases, simply the management of Big Data – undoubtedly makes it possible to make the best of imagined society a reality: autonomous vehicles, facial recognition that helps us identify people, language comprehension to generate voice assistants (which are becoming important when shopping), and image recognition used to identify objects, people, texts, scenes, activities and even emotions! In addition, the automatic analysis of data helps in medical diagnoses, for example, by having a capacity far superior to that of humans when performing repetitive actions continuously over time. In fact, all online platforms already make use of AI: think about how Google organises and presents results, on the most popular social networks and on sales platforms to personalise the shopping experience, which is nothing more than segmenting the target audience to design campaigns and exclusive messages for each client, based on their specific habits and preferences.
The context
So that all of the above can continue growing at the rate of demand, cloud environments have become popular. Thus, most applications are no longer local and DevOps (operations development) joins the deployment of the Internet of Things (IoT) – or rather, a version specific for industry (IIoT) – in a proliferation of connected devices, from toys to household appliances, and all kinds of industrial sensors, and enabling technologies such as 5G (which increases communication speed and decreases latency). A consequence of this is that it increases exposure to cyber risks, and exposes organisations to third party risks by. In other words, it is no longer enough that we are protected ourselves, we have to also demand the protection of our strategic partners.
To respond to this need, a new concept is being implemented in software development, the so-called DevSecOs, which seeks to increase security from the beginning of programming, avoiding subsequent costs by identifying security flaws once the program approaches the final phases or even when it is already in operation. If we have concerns about software that has already been delivered to us, or if we have detected a vulnerability, a good option is to hire a source code audit service, or a Pentest – an intrusion test that is carried out both in a web version and in mobile apps, to detect any errors the program/software may have.
Fuente imagen www.plutora.com
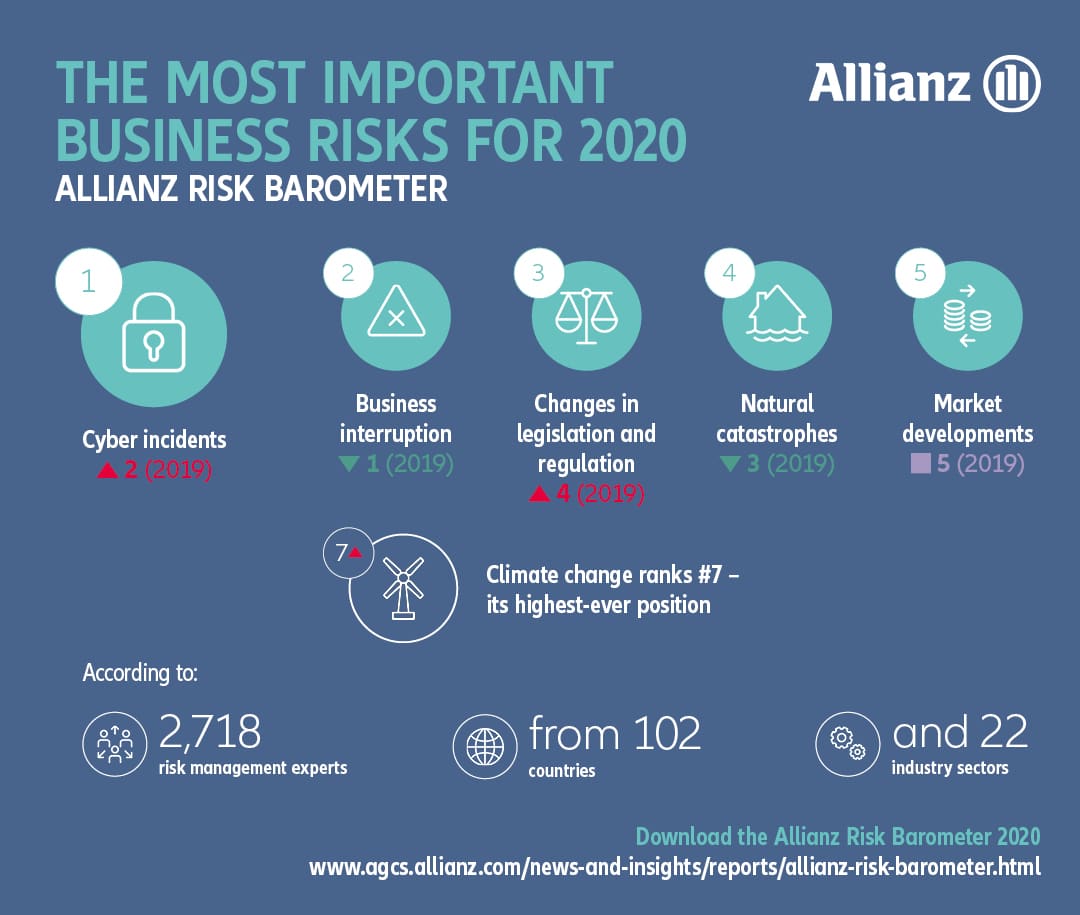
Thus, it is not surprising that cyber incidents have moved on the Allianz Risk Barometer from 15th position in 2013 to 1st position as the most important business risk in 2020, in countries as varied as Austria, Belgium, France, India, Malaysia, South Africa, South Korea, Sweden, Switzerland, the United Kingdom, the USA and Spain, and in sectors including aviation, financial services, government and public services, professional services, technology and telecommunications. The case of aviation is paradigmatic given its complexity, which covers practically all scenarios, and can be perfectly extrapolated to other sectors that are less reliant on cutting edge technology. In this talk as part of the XIII CCN-CERT Conference, Colonel D. Fernando Acero Martín, Director of Cyber-Defence in the Air Force, gives us a very clear idea of the issues and risks to which we are exposed.
Fuente imagen www.agcs.allianz.com
