It doesn't matter the size of the organisation – self-employed, SME or large company – we all have data that, to a greater or lesser extent, is desirable for someone. The other day, I was told about the case of a small petrol station, with three pumps, which tried to make a payment to their supplier, who had told them by email that the account had changed. The employee (who is also the boss, being self-employed) trusted this and made the payment to the new account. It wasn’t a large amount of money for a big company, but it could be the profits of the small petrol station for a year. A few days later, the provider called the boss and asks if they are going to pay...
The provider had been the victim of a cyber-attack and someone, a cybercriminal, was able to read all the emails exchanged with their customers and alter the content of one of the emails at the time the payment for the contracted product or service was to be made. You already know the rest.
The weakest link in security remains people. Sometimes due to ignorance, carelessness or lack of expertise, other times due to malice or unhappiness, perhaps due to that promotion not achieved. It is clear that one of the first steps we must implement is to improve staff training to raise awareness of the risks and consequences of misuse of data and technology.
Except in the case of a member who is angry or “disappointed” by the organisation, such as in the famous case of Edward Snowden, which is difficult to eradicate completely, caution would help to reduce risks. Simple actions would allow us to substantially improve the security of our organisation. Most of the latest cyber-attacks have been via phishing, taking advantage of personal oversights. Regularly reminding the entire team how hackers obtain information or access is highly necessary. Another of the main problems is the exfiltration of data as a consequence, mainly, of not properly carrying out software updates that expose vulnerabilities in systems.
An approximation of the security status of our organisation is easily obtained using the self-diagnosis tool from the National Institute of Cybersecurity (INCIBE). But this is still an approximation, because the complexity of the system grows proportionally with the size and volume of information that the company deals with.
Without a doubt, a change in the prevailing mentality in corporate cybersecurity is necessary
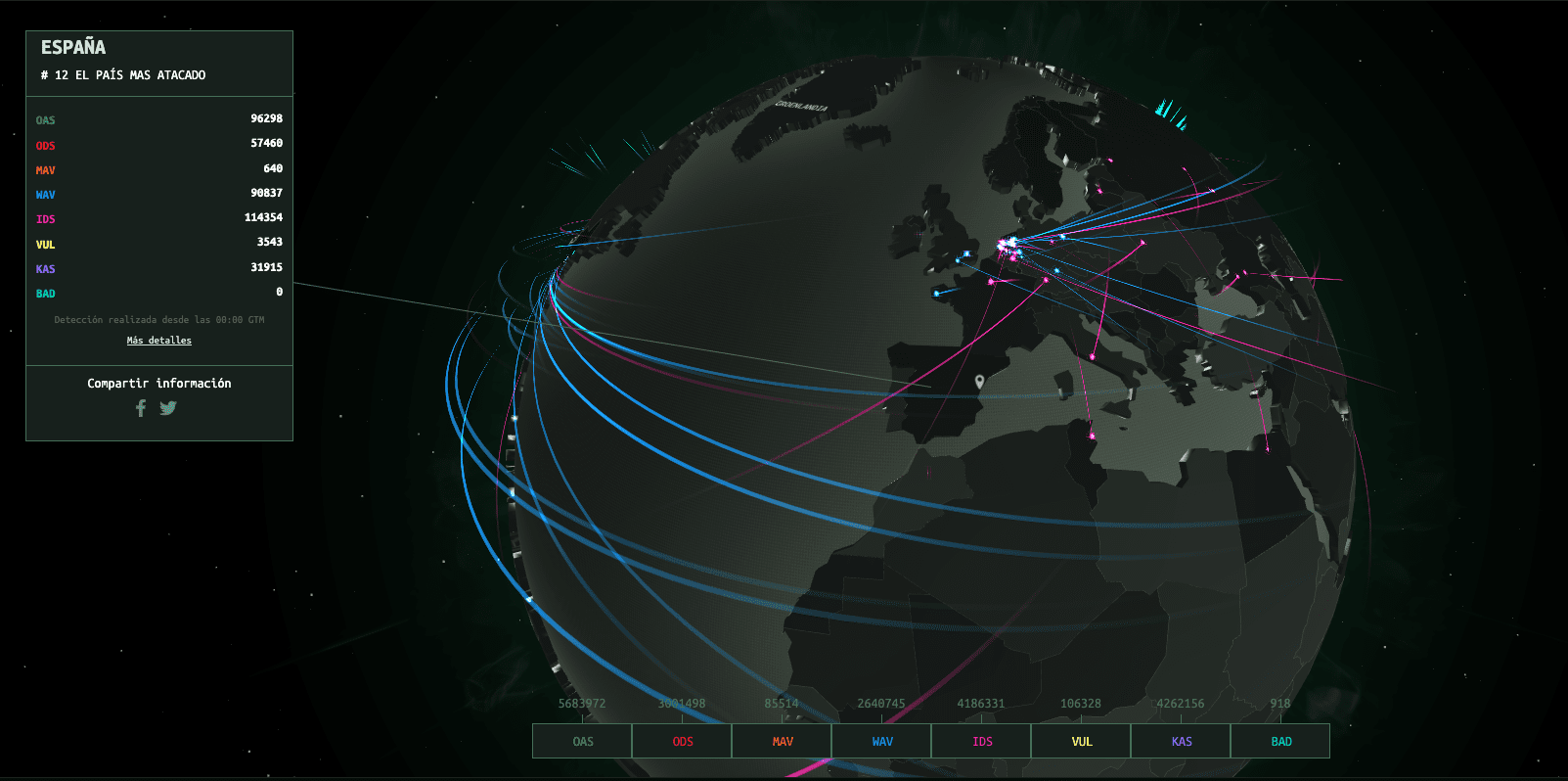
Regardless of the result of the above test, we cannot relax on safety. The Internet is so dynamic that it requires constant attention. A useful test is this real-time map on cyber-attacks.
Detecting if we are part of a botnet (a network with computers remotely controlled by a cybercriminal) can also be very useful for our company and, thanks to INCIBE, it is relatively simple with the following application.
In any case, the above is convenient but not sufficient. The best approach is a risk study by a company that is an expert in cybersecurity with this type of services. This, without a doubt, would suggest situations and problems that we had not even considered.
“The sum of small vulnerabilities and structural and design weaknesses result in a large security problem.”
For example, the obligation to provide a signature of some kind has recently come into force. Some companies have implemented fingerprint readers to control access to facilities and working hours. A pioneering security company, Darktrace, tells of the success story of a planned attack targeting a biometric scanner through a detected vulnerability, which was found in time by this solution.
If the threat had gone unnoticed, the attacker could have inserted their fingerprint data into the database to gain physical access to the industrial plant. The standard antimalware and signature solutions did not detect the subtle activity that led to compromising the physical and logistical security of the company. The interesting thing about Darktrace is that it is a tool based on artificial intelligence and machine learning, which allows the company to anticipate attacks or quickly learn from them to face them alone, without the need to update the signature file for traditional anti malware they work with.
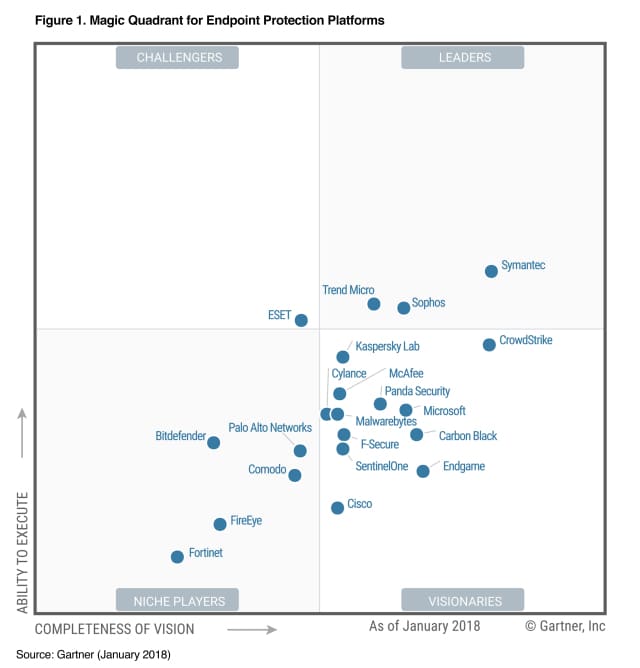
Another interesting and complementary solution to the previous one, insofar as it is more oriented to the end teams (end point) but that is based on the same philosophy as Darktrace, which is very modular and has a native architecture based on the cloud, is CrowdStrike. Seeing its meteoric rise in just two years in the Visionaries section, and approaching Symantec in the Leaders section within the magic quadrant of the Gartner consultancy, it is an application to consider in the event we think about a product of these features.
Many attacks, in addition to the damage they do, have legal consequences. If we manage personal data of European citizens, and we suffer an attack, we have the obligation to report this within 72 hours, according to the General Data Protection Regulation 2016/279 (RGPD) of the European Union. Apart from these and the damage in working hours or absence of it when having to cease production or halt the services we offer, there is another consequence that can even be worse, namely the damage to the reputation of the company.
The attack suffered by Uber in 2017 that exposed 1,500 million user accounts and put at risk the injection of 10 billion dollars by SoftBank or Yahoo, which led to a loss of value in the sale of the company of 332 millions.
The digital transformation is providing us with very powerful solutions, but these can work against us if we do not adapt different business processes to the current security requirements. Given the agility and speed with which everything is now produced and the volume of information that we manage directly or indirectly, any security vulnerabilities, no matter how small, can ruin a job well done.